马上注册,结交更多好友,享用更多功能,让你轻松玩转社区。
您需要 登录 才可以下载或查看,没有账号?注册
×
拓朴如下图
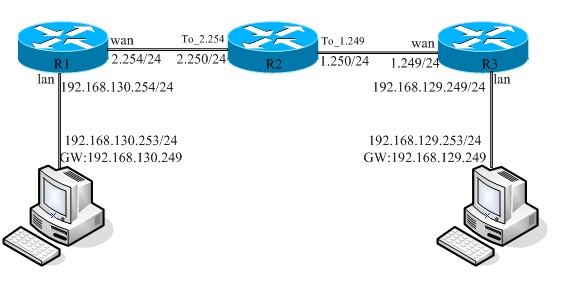
拓朴说明
R3为企业A的routeros,R1为企业A的RouterOS,R2模拟电信局
一、在企业A的ROUTEros上
1、R3上做两条nat规则
[admin@MikroTik] > ip firewall nat print
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat src-address=192.168.129.0/24 dst-address=192.168.130.0/24 action=accept
1 chain=srcnat out-interface=wan action=masquerade
2、做一条缺省路由给电信
[admin@MikroTik] > ip route print
Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o
- ospf
# DST-ADDRESS PREF-SRC G GATEWAY DISTANCE INTERFACE
0 ADC 192.168.1.0/24 192.168.1.249 wan
1 ADC 192.168.129.0/24 192.168.129.249 lan
2 A S 0.0.0.0/0 r 192.168.1.250 wan
3、R3做IPSEC的策略
[admin@MikroTik] > ip ipsec policy print
Flags: X - disabled, D - dynamic, I - invalid
0 src-address=192.168.129.0/24:any dst-address=192.168.130.0/24:any protocol=all
action=encrypt
level=require ipsec-protocols=esp tunnel=yes sa-src-address=192.168.1.249
sa-dst-address=192.168.2.254 proposal=default manual-sa=none dont-fragment=clear
4、R3做对等体的认证,并采用预共享密钥
[admin@MikroTik] > ip ipsec peer print
Flags: X - disabled
0 address=192.168.2.254/32:500 secret="martin123456" generate-policy=no
exchange-mode=aggressive
send-initial-contact=yes proposal-check=obey hash-algorithm=md5 enc-algorithm=3des
dh-group=modp1024 lifetime=1d lifebytes=0
5、做Ipsec 的第二阶段的即ipsec SA,这里采用默认,如果不采用默认,可以新建一个,但是在第三步时
要应用,即 proposal=新建的名字
[admin@MikroTik] > ip ipsec proposal print
Flags: X - disabled
0 name="default" auth-algorithms=sha1 enc-algorithms=3des lifetime=30m lifebytes=0
pfs-group=modp1024
二、在企业B的ROUTEROS上
1、R1上做两条nat规则
[admin@MikroTik] > ip firewall nat print
Flags: X - disabled, I - invalid, D - dynamic
0 chain=srcnat src-address=192.168.130.0/24 dst-address=192.168.129.0/24 action=accept
1 chain=srcnat out-interface=wan action=masquerade
2、做一条缺省路由给电信
[admin@MikroTik] > ip route print
Flags: X - disabled, A - active, D - dynamic, C - connect, S - static, r - rip, b - bgp, o
- ospf
# DST-ADDRESS PREF-SRC G GATEWAY DISTANCE INTERFACE
0 ADC 192.168.2.0/24 192.168.2.254 wan
1 ADC 192.168.130.0/24 192.168.130.254 lan
2 A S ;;; added by setup
0.0.0.0/0 r 192.168.2.250 wan
3、R1做IPSEC的策略
[admin@MikroTik] > ip ipsec policy print
Flags: X - disabled, D - dynamic, I - invalid
0 src-address=192.168.130.0/24:any dst-address=192.168.129.0/24:any protocol=all
action=encrypt
level=require ipsec-protocols=esp tunnel=yes sa-src-address=192.168.2.254
sa-dst-address=192.168.1.249 proposal=default manual-sa=none dont-fragment=clear
4、R1做对等体的认证,并采用预共享密钥
[admin@MikroTik] > ip ipsec peer print
Flags: X - disabled
0 address=192.168.1.249/32:500 secret="martin123456" generate-policy=no
exchange-mode=aggressive
send-initial-contact=yes proposal-check=obey hash-algorithm=md5 enc-algorithm=3des
dh-group=modp1024 lifetime=1d lifebytes=0
5、做Ipsec 的第二阶段的即ipsec SA,这里采用默认,如果不采用默认,可以新建一个,但是在第三步时
要应用,即 proposal=新建的名字
admin@MikroTik] > ip ipsec proposal print
Flags: X - disabled
0 name="default" auth-algorithms=sha1 enc-algorithms=3des lifetime=30m lifebytes=0
pfs-group=modp1024
三、测试
在R3连接的客户机上ping 192.168.130.253 发现能ping 通
并在R3或R1执行 ip ipsec installed-sa print ,能看到协商的数据
以下是在R1上执行的
[admin@MikroTik] > ip ipsec installed-sa print
Flags: A - AH, E - ESP, P - pfs, M - manual
0 E spi=0x86E88506 direction=in src-address=192.168.1.249 dst-address=192.168.2.254
auth-algorithm=sha1 enc-algorithm=3des replay=4 state=mature
auth-key="1f5def8176159e1e90b1771cb14f416e3c7bd142"
enc-key="b97635d9e1174dd2a767305d0c6fd11a252d4ddc0ec36f90" add-lifetime=24m/30m
use-lifetime=0s/0s lifebytes=0/0 current-addtime=feb/02/2007 08:06:00
current-usetime=feb/02/2007 08:06:02 current-bytes=1120
1 E spi=0xF4AD430B direction=out src-address=192.168.2.254 dst-address=192.168.1.249
auth-algorithm=sha1 enc-algorithm=3des replay=4 state=mature
auth-key="00466a0c3ae74e06148acf5078794dd139cf6fc9"
enc-key="8813571d06ce8ed3bdec42c2deb1740039b5dbadfeedc91a" add-lifetime=24m/30m
use-lifetime=0s/0s lifebytes=0/0 current-addtime=feb/02/2007 08:06:00
current-usetime=feb/02/2007 08:06:02 current-bytes=1120
[ 本帖最后由 鑫飘雪 于 2007-2-2 08:33 编辑 ] |
 |Archiver|手机版|小黑屋|软路由
( 渝ICP备15001194号-1|
|Archiver|手机版|小黑屋|软路由
( 渝ICP备15001194号-1|![]() 渝公网安备 50011602500124号 )
渝公网安备 50011602500124号 )